A Brief description of my home network
In this post I will briefly describe my current home network setup.
Basic setup
Lately, I've been pretty busing during my days off with setting up my home network. I'd like to thank my girlfriend for putting up with frequent "I need to restart the router" and other interruptions that came up during the process.
The setup is far from sophisticated for many reasons. Mostly, good network and server equipment is not cheap ;). Furthermore, I have yet to complete some elements of the setup. I will provide more details below.
Here is the basic layout:
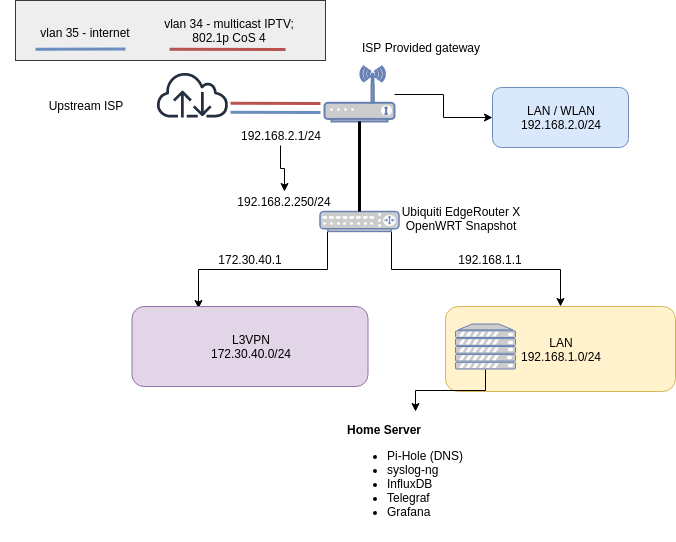
Some brief points to mention:
- The ISP provided gateway has a feature called "Advanced DMZ". Basically, it's a poor-man's-bridge allowing the downstream EdgeRouter X to grab a public /20 DHCP address directly from the ISP.
- On EdgeRouter - WAN iface is vlan 2 to which I've added a static interface
192.168.2.250/24- outside of DHCP range provded by the upstream IPS-provided gateway.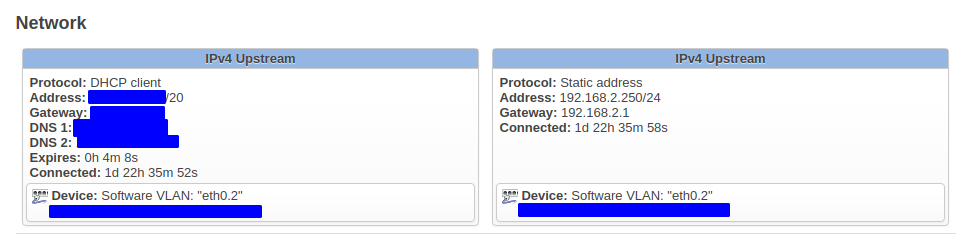
- vlan 1 on the EdgeRouter is LAN
192.168.1.0/24giving out DHCP addresses to the downstream devices within that range. This is where the home server hosting Pi-Hole exists - which takes care of DNS for all devices both within192.168.2.0/24and192.168.1.0/24. To make sure devices in 192.168.2.0/24 can reach the 192.168.1.0/24 network, I've added a static route on the ISP-privided gateway shown in a pic: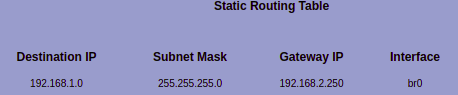 .
. - EdgeRouter X also acts as an L3VPN server/gteway via WireGuard. More on the subject below.
Eventually the plan is to get an APU board to act as firewall + hosting PiHole; a simple managed L2 switch and wireless APs to move everything over to the EdgeRouter X, completely bypassing the ISP's gateway.
Home server
For the time being I've repurposed an old laptop to be a home server. It's running Manjaro Linux. I've thought of installing Ubuntu Server first, but having AUR is such a nice bonus. Furthermore, Pacman is by far my favourite package manager - hence I opted for Manjaro. Arch would have been a better choise perhaps, however at the time of setting things up speedy setup was a higher priority.
Pi-Hole
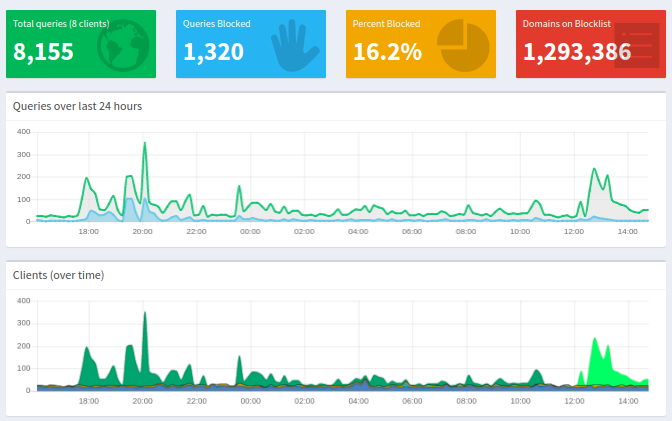
The home server is hosting Pi-Hole for network wide ad-blocking. If you are not familiar with Pi-Hole, I encourage you to check it out - a great project. My favourite features are insight into DNS queries on the network (who knew how much junk Samsung TVs send), and awesome graphs showing a nice overview of DNS traffic.
Syslog-ng
On a fine spring evening I've decided to check the syslog on EdgeRouter. Perhaps unsurprisingly, there were tons of IPTABLES REJECT messages of random IPs scanning my ports. It would be a shame is this information was lost after rebooting the ERX, so I've installed syslog-ng on my home server. The ERX is configured to send all syslogs over to the server, which are stored in /var/log/network/router-ip/year-month-day/messages file. It was a matter of writing a quick bash script to filter the logs by REJECT querie, extract IPv4 addresses only, remove duplicates, filter out private LAN 192.168.2.0/24 IPs and build a master blocklist - drawing some inspiration from Fail2ban. The master blocklist is then sent to a GitHub gist a few times every day.
The ERX router has a cron job going to download the latest copy of the blocklist daily and add the IPs to the blacklist.
You can check out the original script here and the master blocklist here. Already at 22297 unique addresses. Wow!
TIG Stack
Finally, the home server is running a TIG Stack (Telegraf, InfluxDB, Grafana) to collect basic information about the home server. Currently, it's monitoring DNS queries using Pi-Hole APIs and some general linux host stats of the home server - CPU, memory, load average, etc. You can check the dashboards out here and here.
Secutiry
Finally, I wanted to mention the ERX is running BCP38 to block bogus forged ingress prefixes. Perhaps an overkill, it was easy to implement and makes me sleep better :). Of course the defaul firewall policy on ERX is to deny an ingress traffic unless explicitly allowed. SSH logins with password have been disabled on both ERX router and home server and the ports on which OpenSSH server listens on have been changed.
Speaking of OpenSSH - by default OpenWRT comes with dropbear as an SSH server - which I've disabled an installed OpenSSH instead. I've opted not to use RSA key, instead going for ED25519.
WireGuard
For those unfamiliar with WireGuard, WireGuard is a layer 3 network tunnel. It uses Curve25519 points as pre-shared static keys to achieve mutual authentication, drawing it's inspiration from OpenSSH. For more information check out 1,2,3,4.
Spinning up a WireGuard server instance is a piece of cake. One of my ongoing projects is specifically designed to automate a large portion of the process. Check it out - WireGuard-Ligase.
At the time of writing, I've got three WireGuard servers running. Two of them run as Ubuntu 18.04/CentOS 7 servers on Amazon EC2 - one in Montreal, the other on Ohio. The third one is setup on my home EdgeRouter X. While the EC2 instances are for mostly for testing purposes, the server hosted on my home router is for daily use.
Why would I host a WireGuard server from home?
- Fist, we all know about how sketchy public WiFi is. Having a secure tunnel to my home network make it much harder to snoop my traffic.
- Second, remember Pi-Hole? Guess what, with a WireGuard tunnel to my home router, my devices can take advantage of Pi-Hole ad-blocking from anywhere. So no matter where I am, even using my cellphone data, my adds are blocked.
- Finally, it's a nice bonus to be able to access my home devices remotely without worrying about security too much.
One of the challenges of setting up a server at home is due to not having a static address. My ISP DHCPs a public IPv4 address over to my ERX, which may change at any time. For now, I've written a quick script on my server to check the public IP address a few times a day and to save it to a private github gist. If the address changes, all I'd have to do is check out the gist and update a client config on my devices. Not too difficult.
References
[1] - https://github.com/SirToffski/WireGuard-Ligase/wiki/About-the-project - Wiki for my WireGuard-Ligase project.
[2] - https://www.wireguard.com/ - Official WireGuard website.
[3] - https://www.wireguard.com/papers/wireguard.pdf - a whitepaper by WireGuard founder and lead developer - Jason A. Donenfeld
[4] - https://hal.inria.fr/hal-02100345/document - a formal research paper presenting the first mechanised cryptographic proof of the protocol underlying WireGuard.